Improving Cyber Security for Physical Security
The push to add better Cyber Security to Physical Security is driving a major industry trend towards Hybrid Cloud Systems.
Hybrid Cloud Physical Security Platforms Gain Traction because of Cyber Security
The big trend for 2023 has been the shift to hybrid cloud based physical security platforms. Similar to the shift that happened in the 2010s when most of the industry moved from analog to HD, the shift to hybrid cloud will define the industry for the next decade. This quarter, however, the cyber security improvements inherent in a hybrid cloud approach took forefront.
What's driving the market to adopt hybrid cloud systems?
One Login for All Your Camera Brands / Locations
Increase Cyber Secure of Existing Hardware
Use of AI to Reduce False Alarms & Alerts
What's Cloud in Hybrid Cloud Physical Security?
Hybrid cloud systems can be confusing. Many people think the "cloud" in "Hybrid Cloud Physical Security" means that the storage is in the cloud. Although this is often offered, this is not the main driver of the move to the cloud - or what is most valuable in switching to a hybrid cloud based approach.
Hybrid cloud systems move the application interface to the cloud - not necessarily the footage storage. By moving the "software you log into and use" off the local area network and to the cloud, this frees IT personel up from having to manage firewalls or VPNs for remote access. This vastly increases the cyber security of your local network.
SCW's hybrid cloud platforms are: survail which replaces an NVR for video surveillance or Openpath / Avigilon Alta for access control. These systems move the login and user interface application to the cloud, making it so that you no longer have to open ports, run a VPN, or otherwise manage remote access for full on prem systems, like NVRs or legacy access control systems.
Camera as Weapon - Not Target
Malicious actors have found physical security devices to be fertile ground for malware. It is estimated that over 1 Million Dahua / Lorex cameras have been infected by the Bashlight malware. Another one and a half billion devices (cameras and lower cost routers) are estimated to be a part of the Mirai botnet. Mirai started as an old-school racketing play by a fraudulent cyber security company ("Buy my DDOS protection or get DDOSed") but now the Chinese and Russian governments have each forked the source code and control some of the devices that are infected. These devices are now being weaponized by foreign governments, which is partly why Congress recently banned several security camera equipment manufacturers from federal jobs.
Most hacks are designed to either disrupt a companies operation by encrypting their data and then forcing them to pay a "ransom" to unlock it or to steal valuable information like identities, credit card numbers, or source code. Many people improperly assumed that there wasn't a big cyber risk from a security device getting hacked, because there's not much data like that in video surveillance footage.
However, that's not how Miari or other IOT malware works. IOT malware treats the IOT device (in this case a camera) like the weapon in an attack - not as the target of the attack. In the accompanying image, you can see how the Mirai malware uses an unsecured camera to infect other devices on the network.
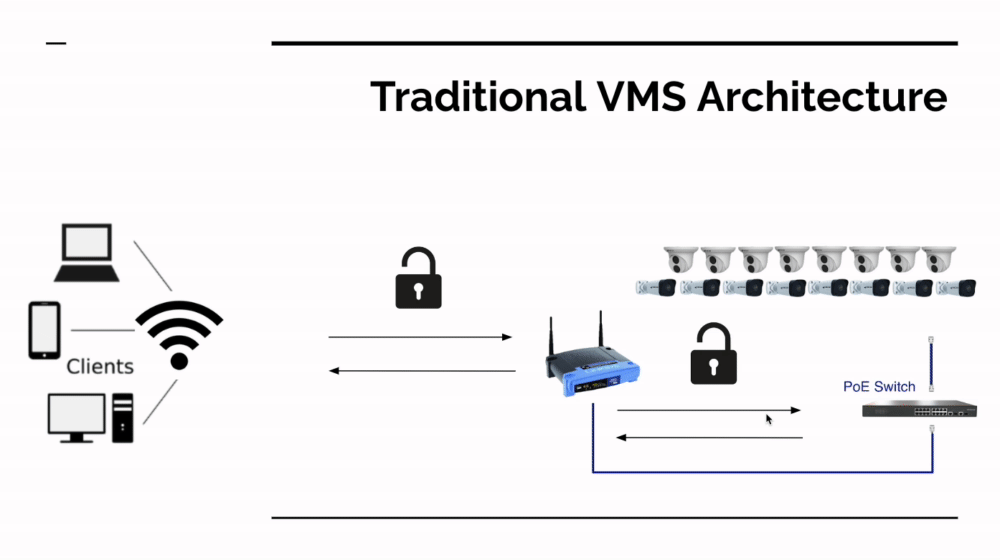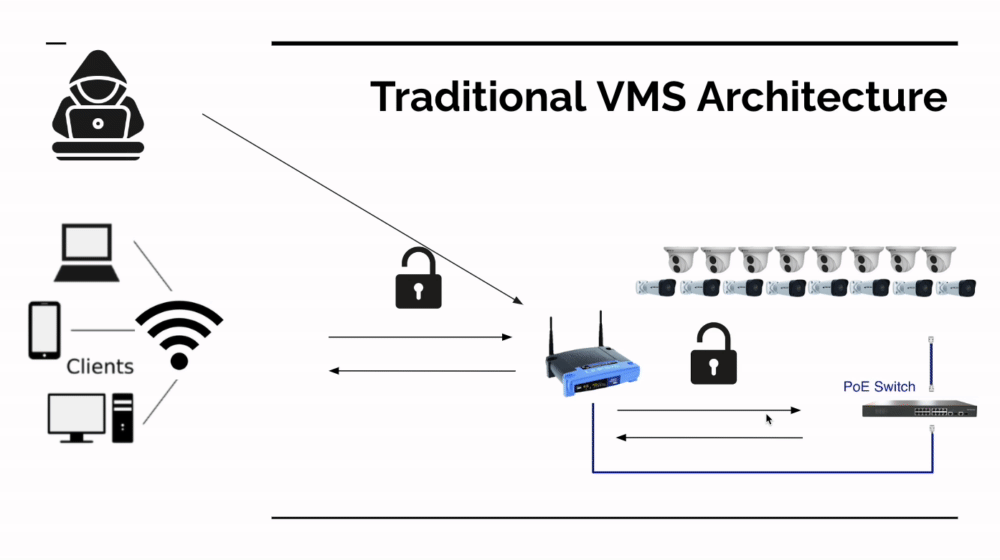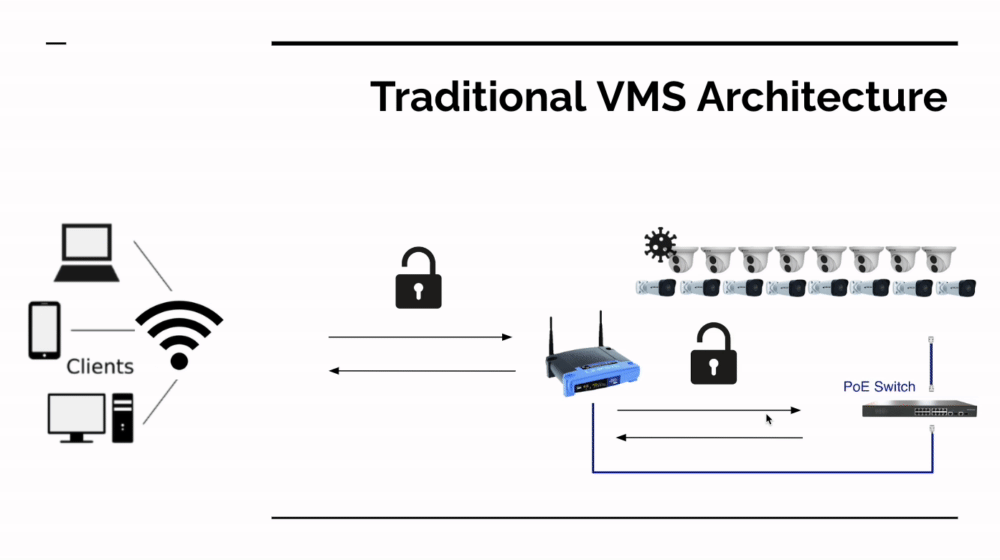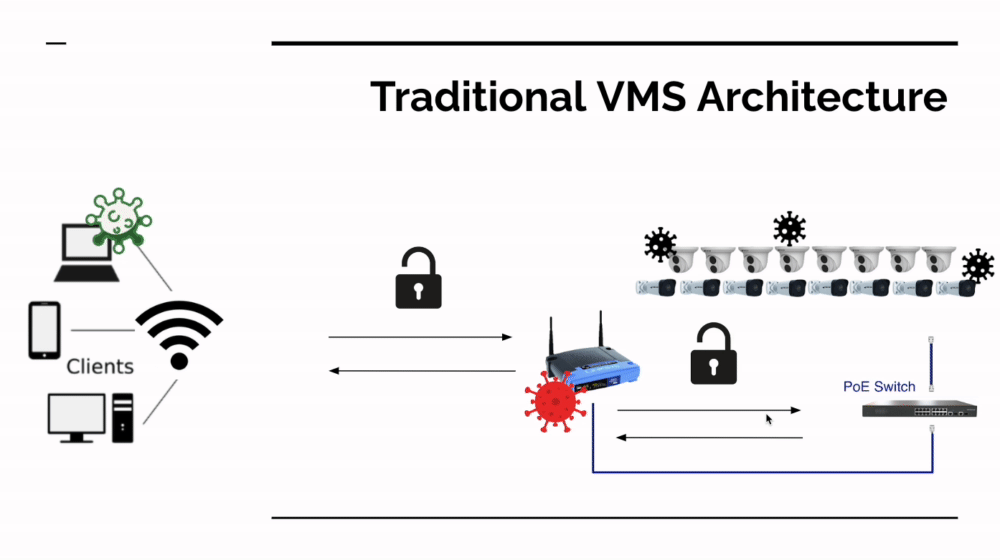
These Attacks Evade How Firewalls and Malware Protection Work
Most traditional network security services (firewalls and virus checkers) are designed to monitor traffic coming into the network from the outside, look for threats, and try to block them. Some higher end network scans, such as our endpoint protection, watch for traffic malicious code moving around inside the network, but many firewalls do not.
Similarly, IOT devices (including cameras, but also many other things like smart thermostats) are notoriously hard to protect from viruses and other malware because unlike a Desktop environment, you can't install run a virus checker on them. If you do find a virus, it can be very difficult to remove, as there's often very little support from the manufacturer. There are even some lower end cameras that ship with malware.
An unsecured camera (for example, one that has an open port and no ip address restrictions on who can talk to that device) can be used to distribute problematic code elsewhere on your network. Sometimes, the hacker watches for a user to log in with the camera credentials, and the copies those credentials and installs a malicious firmware file through the normal camera firmware management tools; sometimes they find a way to bypass the login through an exploit.
The Architecture Differences of a Hybrid Cloud Approach
Survail and Openpath's Hybrid Cloud-based platform models move the application interface to the cloud. This enables the use of one-way data - meaning there's no open inbound access to your network to view footage or open doors required. In addition, this approach also has these benefits:
Firewall: no holes
VPN: built-in
MFA: built-in
Zero Trust: built-in
Automatic Updates: built-in
VLANS: built-in, hardware based
Device Logs: built-in
IP Address Exclusion: built-in, server enforced
Password Rotation Policies: built-in, server enforced
Encryption: built-in
In the accompanying image, you can see how a hybrid cloud based system communicates. When an event occurs (a door is locked or a video event is created) it send data to a file storage server over an encrypted connection to HTTPS-authenticated file storage server (but that doesn't talk back to the local network). When the user logs into the application interface, they use an encrypted connection to talk to the server - not the on premises cameras or hardware (again, this doesn't require any inbound connections the local network).
If the user wants to watch live feeds of cameras or our devs want to push a firmware update, the application talks to one of many hidden, secret servers which are not exposed to the outside internet or known to application users.
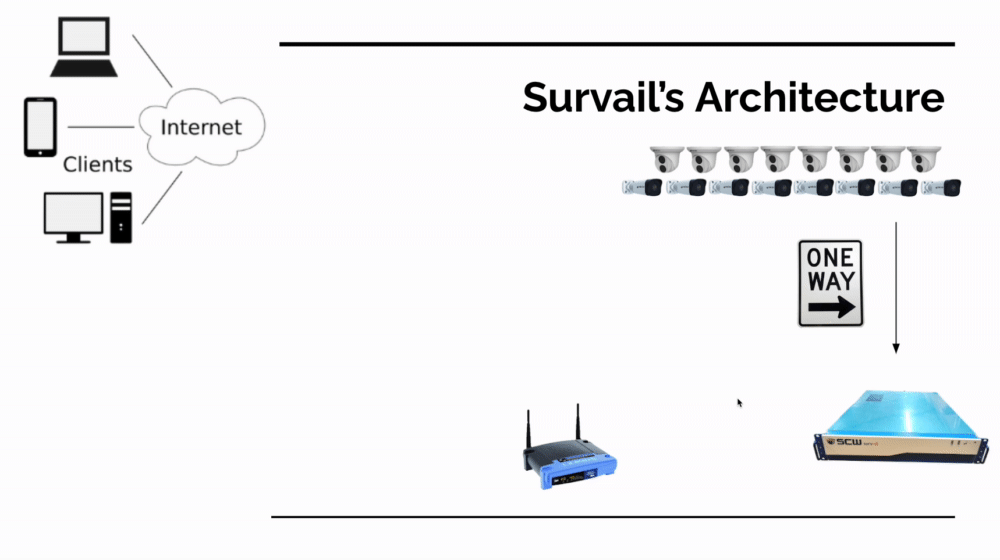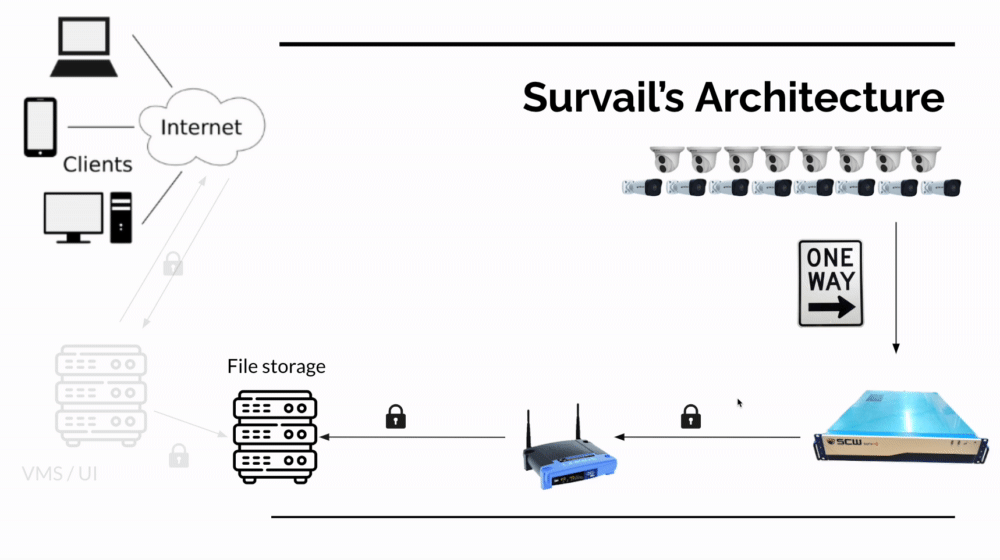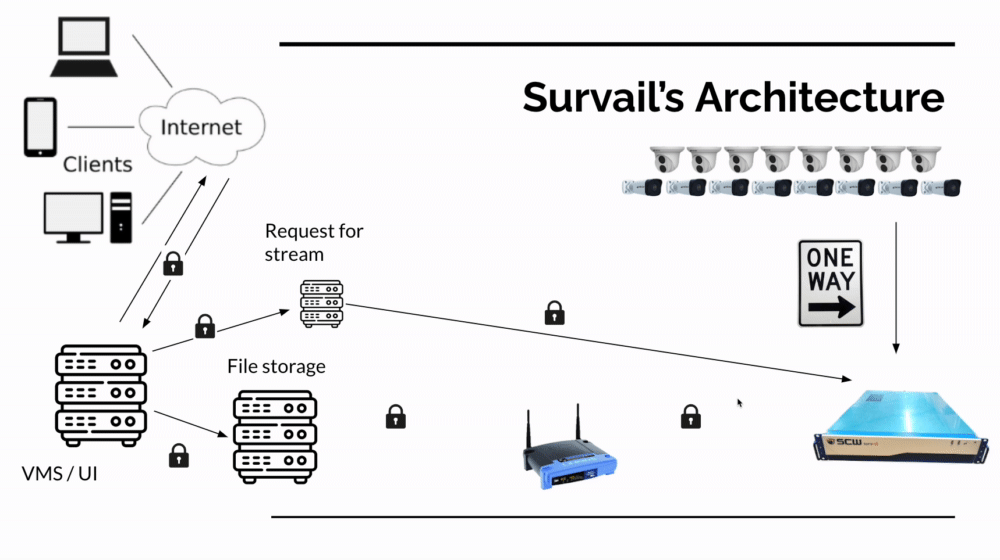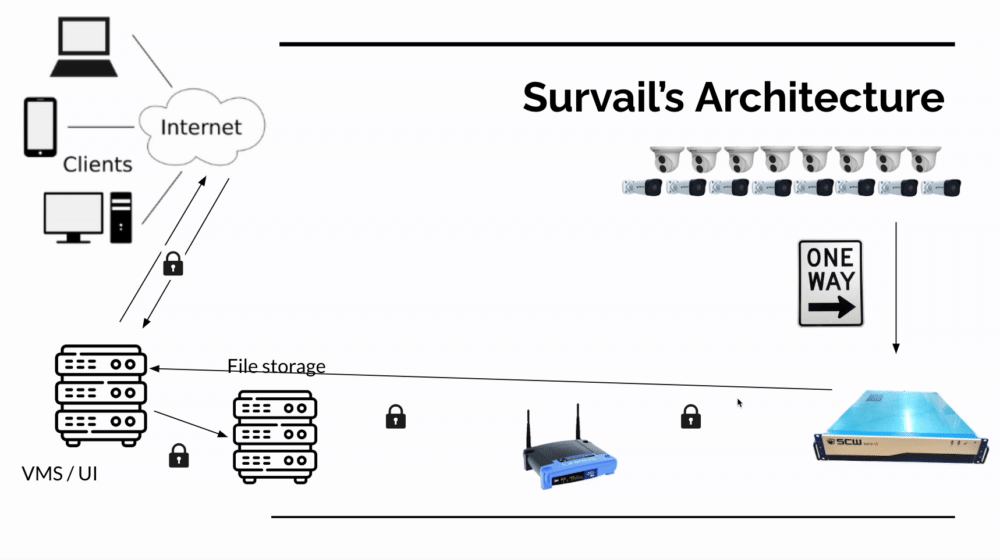
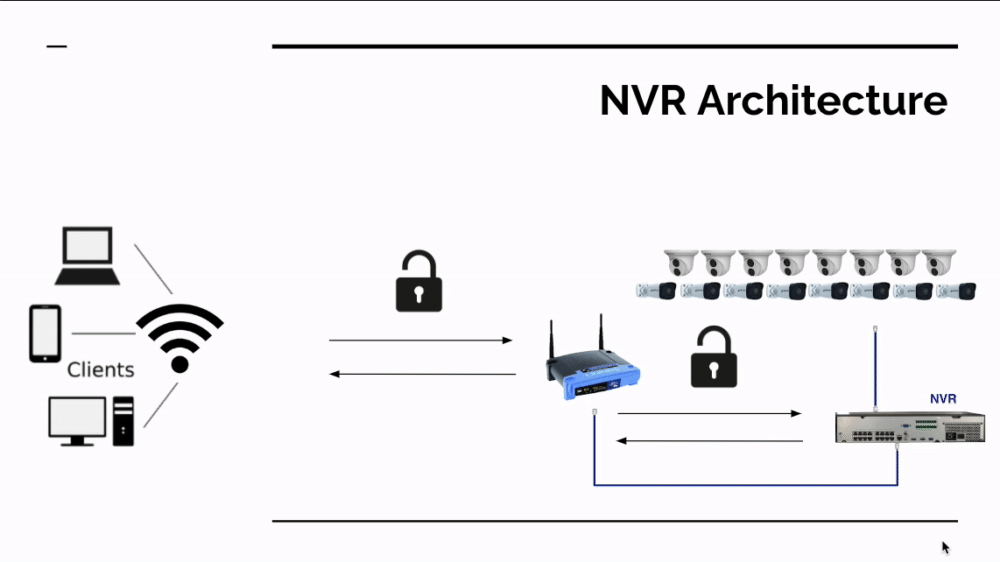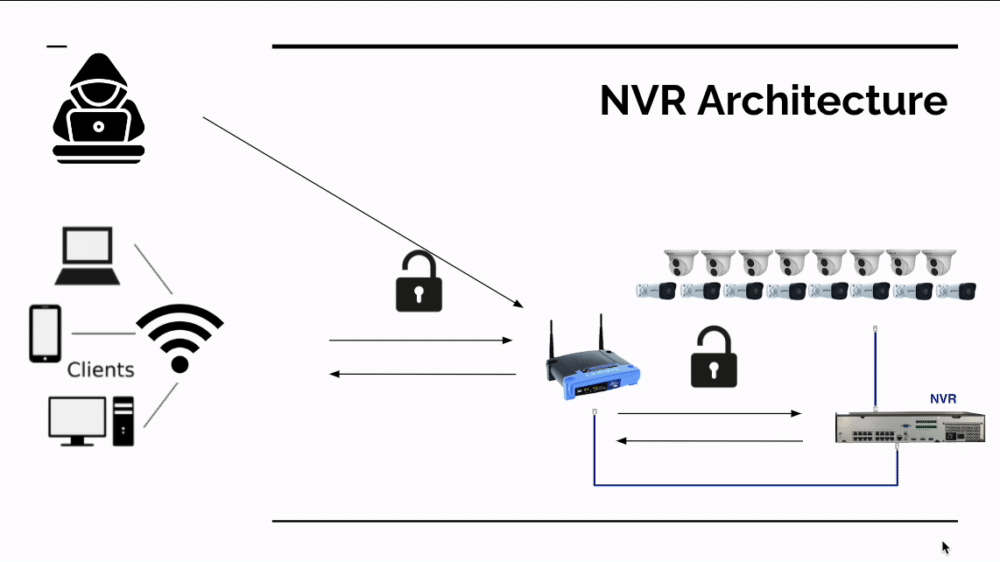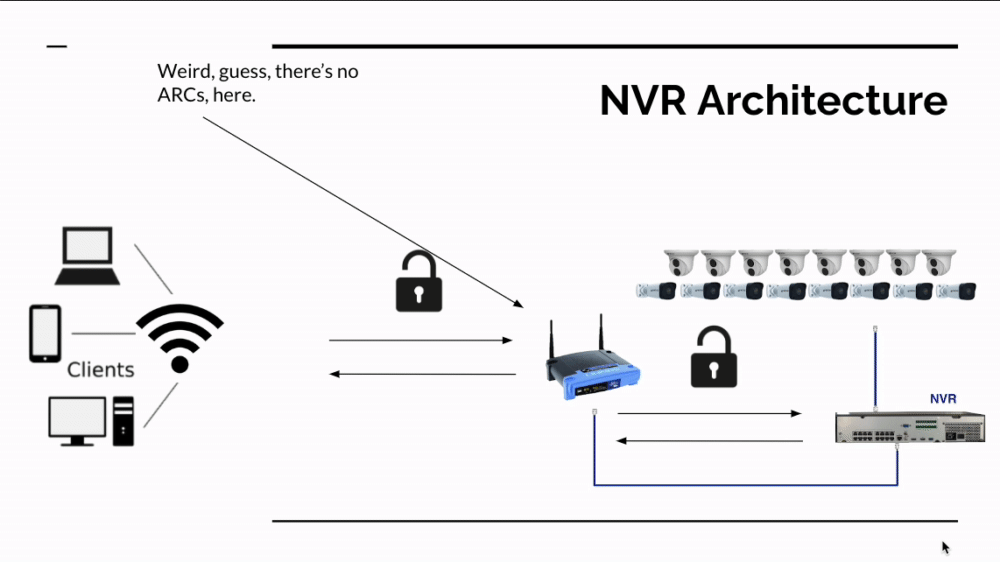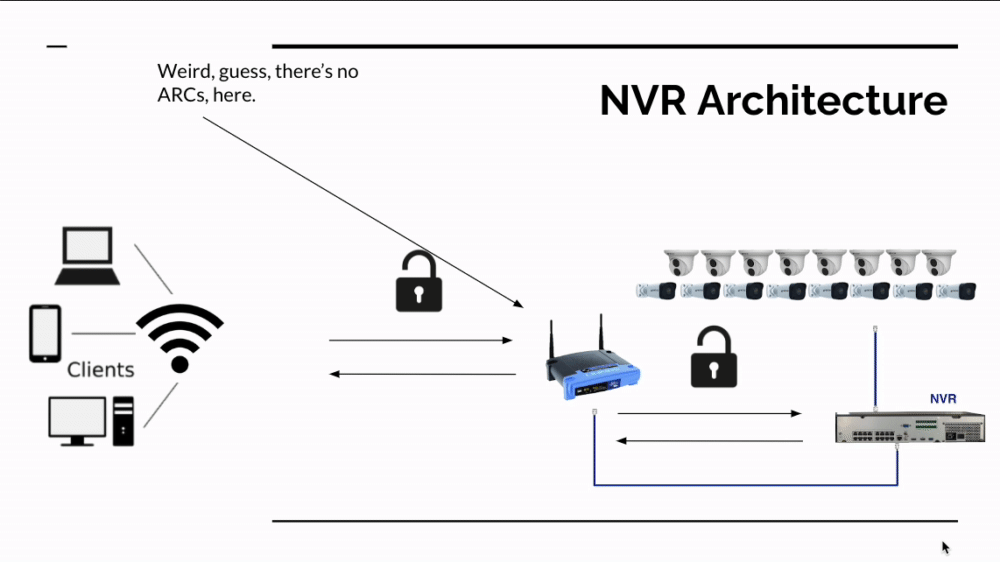
SCW NVR Subnet Design
The first goal in any cyber security plan is to reduce your threat footprint. If you have fewer devices on a network, there are fewer things that can be hacked. Properly connected, SCW NVRs will do this for you.
The cameras plugged into the Admiral line NVR's POE ports directly or plugged into the Imperial Line NVRs Lan2 Network directly are not visible or accessible on your computer network. They run on an isolated network. The only way to access these cameras is to plug a computer into those POE ports.
Having fewer devices remotely accessible is always a good thing for cyber security, so a NVR centered design is certainly far more secure than putting cameras on the network. There's also an additional (however lucky) benefit to having an NVR in the way: Mirai currently only runs on ARC processors not ARM or x86 (Intel) processors. In the accompanying image, you can see what currently happens if Mirai attacks an insecure network with a SCW NVR - it doesn't find a device that can run Mirai.
This is a happy accident; not a long term solution. If you choose to go with an on premises solution, you still need to protect your network if you enable remote access. Now that the Mirai source code is in the wild and being used by hostile foreign governments, we expect it to morph and attack additional CPU architectures.
Trusted vs Semi-Trusted Network Design
The FBI has released a bulletin that recommends that you keep your IoT devices, like security cameras, on a separate network from your computers. You can accomplish this physically with two physical networks or virtually with a VLAN (virtual local area network).
We advise either creating a second, physically separated network or VLANing any "less trusted" devices (what I mean by this is any device that can run code, but can't run virus checking software, such as thermostats, cameras, access control units, industrial sensors, etc) and splitting them from your trusted network (where PCI, HIPAA, trade-secret or operational data may pass thru).
Secure Remote Access
There are many ways to connect to your camera system remotely. Using a VPN is your best option.
Update Firmware
Make sure you keep your firmware up to date.
