Strategic Security Solutions for Multi-Location Enterprises
Table of Contents
Intro:
Strategic Security Solutions for Multi-Location Enterprises
The Evolving Landscape of Security in Multi-Location Settings
KO Storage: A Model for Multi-Location Security Excellence
Unifying Vision with Technology: The SCW Approach
Chapter 1:
Understanding Multi-Site Security Needs
Multi-Building Units
Multi-Floor Buildings
Dispersed Sites
Identifying Common Threats and Security Goals Across Industries
Chapter 2:
Infrastructure Essentials for Multi-Site Security
Network Considerations
Physical Equipment Requirements
Examples of infrastructure setups
- A Car Dealership with 3 Locations
- A University with Multiple Buildings and Floors
Chapter 3:
Advanced Surveillance Systems
CCTV and IP Camera Systems
Comprehensive Coverage Strategies
Integration with Centralized Management Software
Chapter 4:
Access Control and Alarm Systems
The Role of Alarm Systems
Adapting Principles Across Industries
Chapter 5:
Implementing a Unified Security Strategy
Developing a Unified Security Strategy
Importance of Scalability, Flexibility, and Remote Management
Implementing the Strategy
Chapter 6:
Maintenance, Monitoring, and Response
Ongoing Maintenance and Updates
Monitoring Services
Developing a Response Plan
Chapter 7:
Future-Proofing Multi-Site Security
Anticipating Future Security Challenges
Leveraging Technological Advancements
Staying Ahead of Security Trends
Chapter 8:
The Secret to Securing Your Enterprise
Strategic Security Solutions for Multi-Location Enterprises
As the need for reliable security continues to increase, the need for comprehensive, strategic security systems across multiple locations has never been greater. Especially for businesses looking to expand.
As businesses grow, the complexity of safeguarding assets, information, and people increases with it.
In this e-book, we explore the intricacies of crafting effective, scalable and adaptable security strategies that can be tailored to the unique demands of each site.
Key takeaways from this guide:
The importance of tailoring security strategies to specific site requirements
Leveraging centralized management for oversight
Future-proofing against evolving threats
The Evolving Landscape of Security in Multi-Location Settings
In today’s modern world, the business landscape is one of rapid expansion and diversification. Today's enterprises operate across multiple locations, each with its own unique security requirements. The challenges are multifaceted, with the need to protect physical assets, intellectual property, and personnel across various geographical and operational environments.
This level of complexity needs a holistic approach to security, one that integrates cutting-edge technology, strategic planning, and a deep understanding of the specific contexts of each location.
KO Storage: A Model for Multi-Location Security Excellence
KO Storage's case study highlights many of the challenges that multi-location enterprises face. With its unique operational model and customer interaction, this sector highlights the importance of tailored security solutions.
Through the lens of KO Storage, a family-owned business experiencing exponential growth, we explore the practical aspects of deploying a security system that addresses present needs and anticipates future challenges.
Since its inception in 2016, KO Storage has grown rapidly to now operate over 100 facilities across 24 states. As impressive as this growth was, it also presented a number of significant security challenges. Each facility, with its unique layout and storage offerings, from mini-indoor containers to extensive outdoor spaces for vehicles, needed its own custom security solution. The company faced the daunting task of integrating disparate security systems, managing access across numerous sites, and ensuring comprehensive coverage to prevent theft, damage, and liability.
The turning point for KO Storage came when they partnered with SCW (Security Camera Warehouse) in a move that aligned their strategic vision with technological expertise. SCW's holistic approach not only addressed the immediate need for high-quality camera systems but also the broader requirements of scalability, ease of management, and cost-effectiveness.
Unifying Vision with Technology: The SCW Approach
To solve the challenges KO's rapid growth had presented, SCW provided them with a unified platform that streamlined credential management and enhanced visibility across all locations. This solution was not merely about installing cameras; it was about understanding KO Storage's operational dynamics, anticipating future needs, and crafting a system that could evolve with the company.
Key Principles of a Good Multi-Location Security Partnership:
Customization and Flexibility: Understanding that each location has unique security needs and requires a tailored approach.
Scalability: Deploying systems that can grow and adapt to future expansions.
Integration: Offering a single-source platform for ease of management and consistency across locations.
Quality and Durability: Investing in commercial-grade equipment that ensures reliability and longevity.
Support and Service: Providing ongoing support to ensure the optimal functioning of the security systems.
As we dive deeper into network administration, facilities management, and loss prevention in the following chapters, we’ll provide you with actionable insights and practical guidance to help you solve your multi-location security challenges.
Understanding Multi-Site Security Needs
As your business grows and diversifies, your operational landscape often expands into multi-site environments, with each site presenting a unique set of security challenges. From multi-building units across extensive campuses to dispersed sites stretching over vast geographical areas, the complexity of securing these assets increases significantly.
In this chapter, we dive into the intricacies of multi-site security, shedding light on the common threats most industries face and the security goals they set.
Multi-Building Units
Multi-building units are common in industries such as manufacturing, education, and commercial real estate. They require a comprehensive approach to security as they may encompass separate facilities for different operational purposes—production lines, administrative offices, research labs, and storage areas—each with its own specific security considerations.
The primary challenge lies in creating a seamless security network that offers centralized control while catering to the unique needs of each building.
Common Threats Unauthorized access, theft of materials or intellectual property, vandalism, and safety hazards.
Security Goals: To establish a controlled environment where access is regulated based on roles, ensuring the safety of personnel and protection of assets, and to implement robust surveillance that can monitor multiple locations simultaneously.
Multi-Floor Buildings
Multi-floor buildings, common in sectors like healthcare, government, and corporate offices, present a vertical dimension to the security challenge. Here, the focus shifts to managing the flow of people—employees, visitors, patients, or clients—through various levels, each possibly designated for different functions or levels of security clearance.
Common Threats: Tailgating into restricted areas, internal theft or sabotage, and ensuring the safety of occupants in case of emergencies.
Security Goals: To enforce access control measures that restrict movement between floors, deploy surveillance systems that cover common areas and entry points, and integrate alarm systems for emergency evacuations or alerts.
Dispersed Sites
Industries like logistics, energy, and agriculture often operate across dispersed sites separated by significant distances. These sites, including warehouses, farms, solar farms, or logistical hubs, pose a challenge in terms of consistent security monitoring and management.
Common Threats: Theft of goods or equipment, trespassing, environmental damage, and the logistical challenge of quick response times by security personnel in case of incidents.
Security Goals: Implement remote monitoring capabilities, ensure that security personnel can oversee all sites from a centralized location, and use advanced analytics to detect irregular activities or breaches in real-time.
Identifying Common Threats and Security Goals Across Industries
While the settings and specific challenges may vary, certain security threats loom large across all multi-location settings. These include unauthorized access, theft, data breaches, vandalism, and the overarching need for environmental safety and regulatory compliance.
As a result, the overarching security goals remain consistent: protect people, safeguard assets, ensure operational continuity, and maintain regulatory compliance.
In crafting security strategies for multi-location enterprises, it’s crucial to assess the specific needs and vulnerabilities of each site while also considering the synergies that can be leveraged through unified security solutions. Whether through physical security measures, technological tools, or a combination of both, the aim is to create a secure, resilient operational environment that supports the business's objectives and growth ambitions.
Throughout this ebook, we explore strategies, technologies, and best practices that can help businesses meet these multifaceted security challenges, drawing on real-world examples and expert insights to guide the way.
Infrastructure Essentials for Multi-Site Security
Multi-site security relies heavily on a well-designed infrastructure that can accommodate each location's unique requirements while providing seamless integration and centralized control.
In this chapter, we provide an overview of the essential components of such an infrastructure, focusing on network considerations and physical equipment requirements. We work through these considerations highlighting examples from a car dealership with multiple locations and a university campus.
Network Considerations
A robust network forms the backbone of any modern security system, especially in multi-site setups where connectivity and data flow are crucial. The network must support high volumes of data traffic, provide reliable connectivity across all locations, and ensure secure data transmission to prevent unauthorized access or breaches.
Key Network Considerations:
- Bandwidth and Speed: Enough to support live video feeds, data uploads, and downloads without lag or downtime.
- Redundancy: Failover mechanisms and backups to maintain operations in case of network failures.
- Security: Advanced encryption, firewalls, and secure VPNs for remote access to protect against cyber threats.
- Redundancy: Easily expandable to accommodate new sites or upgraded technologies without overhauling the existing infrastructure.
- Data Segregation: internal HR and operational data, Customer data, and IOT data should not be able to commingle, they should each be on their own subnet, physical network, or VLAN.
Physical Equipment Requirements
The physical components of a multi-site security system include surveillance cameras, access control units, sensors and alarms, and the necessary hardware for data storage and processing.
To effectively cover all critical areas, it’s crucial to not only select the right equipment but strategically place it.
Essential Equipment:
- Surveillance Cameras: A mix of fixed, PTZ (pan-tilt-zoom), and speciality cameras tailored to specific site needs.
- Access Control Systems: Card/fob readers and electronic locks for regulated site access.
- Sensors and Alarms: Motion detectors, door/window sensors, and environmental monitoring for comprehensive security coverage.
- Network Infrastructure: Switches, routers, and servers optimized for security applications and data handling.
Some Examples of Infrastructure Setups
Automotive
Car dealerships require a security setup that protects valuable inventory across different sites while allowing for smooth day-to-day operations. To maximize protection, each location is equipped with high-definition cameras covering showrooms, lots, and service areas.
Wireless connectivity between cameras and the central monitoring station facilitates real-time surveillance across all sites. Access control systems regulate entry to inventory storage and employee-only areas, with activity logs accessible from a centralized management platform.
Network redundancy ensures continuous operation, with cloud-based data storage offering additional security and accessibility.

A University with Multiple Buildings and Floors
A university campus presents a complex security challenge, as multiple buildings, including academic halls, dormitories, and administrative offices, must be secured. To solve this, a fiber-optic network is used to seamlessly connect all campus buildings, providing the bandwidth needed for high-resolution video streaming and data transfer.
Surveillance cameras with wide-angle and zoom capabilities are installed at building entrances, corridors, and common areas, with special attention to dimly lit paths and parking lots.
Multi-layered access control secures residential halls and sensitive areas, integrating with student ID systems for seamless operation.
Emergency call stations and mass notification systems enhance safety measures, ensuring swift communication in critical situations.
Building a security infrastructure for multi-site operations requires careful planning and consideration of both technological and physical components.
In the following chapters, we dive deeper into the technologies and strategies that make these setups possible, guiding you through the process of creating an effective and scalable multi-site security system.

Advanced Surveillance Systems
In multi-site security, advanced surveillance systems play a pivotal role in ensuring comprehensive coverage and real-time monitoring.
In this chapter, we explore cutting-edge surveillance technologies tailored for multi-site operations, focusing on CCTV and IP camera systems and the crucial role of centralized management software, with ViewStation serving as a prime example.
CCTV and IP Camera Systems
CCTV (Closed Circuit Television) and IP (Internet Protocol) cameras are at the heart of modern surveillance strategies, each offering unique benefits to multi-site security infrastructures.
CCTV Systems are traditionally known for their reliability and wide-ranging coverage. Operating on a closed network, they’re less susceptible to cyber threats. CCTV systems provide a steady, dependable surveillance solution for multi-site operations where internet connectivity may be inconsistent.
IP Camera Systems represent the evolution of surveillance technology, capable of seamlessly transmitting video footage over the internet. This allows for higher video quality, remote access, and the ability to integrate with other security systems. For multi-location enterprises, IP cameras offer the flexibility of monitoring all sites from a centralized location, making them ideal for expansive operations.
Comprehensive Coverage Strategies
An effective combination of fixed, PTZ, and specialized cameras is critical to achieving comprehensive surveillance coverage, especially in multi-building and multi-floor locations.
Equipment for Coverage
Fixed Cameras provide constant coverage of specific areas, such as entrances, parking lots, and high-value inventory zones.
PTZ Cameras offer the versatility to pan, tilt, and zoom, allowing security personnel to actively monitor and investigate suspicious activities in real-time.
Specialized Cameras, including thermal imaging and low-light cameras, ensure surveillance effectiveness under challenging conditions, such as darkness or extreme weather.
Integration with Centralized Management Software
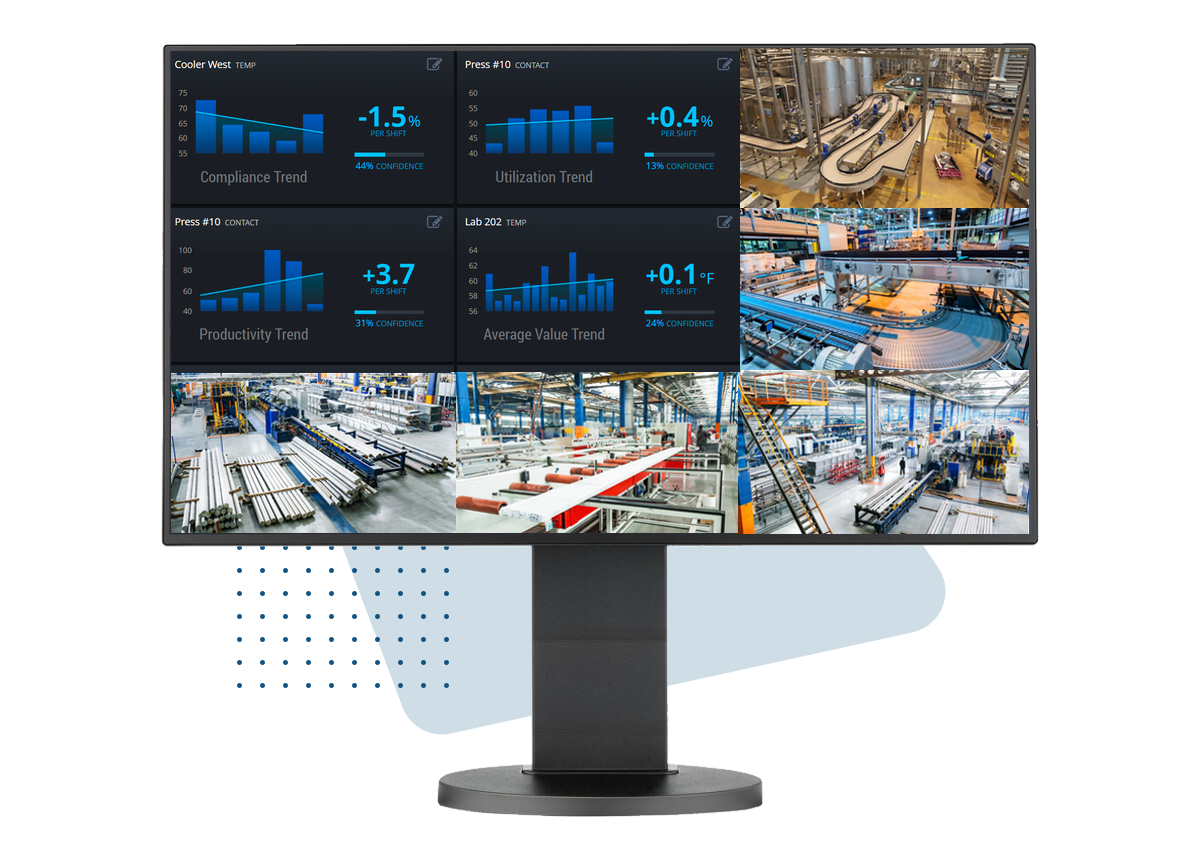
The integration of surveillance systems with centralized management software is crucial for efficiently monitoring and managing multi-site operations. By using this software, security managers are able to view live feeds, review recorded footage, receive notifications, and manage system settings on a single platform, enhancing overall security.
ViewStation: Comprehensive Cover. Centralized management
ViewStation provides centralized management to multi-site surveillance managers right across the globe. It provides a unified interface for managing video feeds from both CCTV and IP camera systems across various locations.
Key features include:
Multi-View Capability: Simultaneously monitor live feeds from multiple cameras across different sites, improving situational awareness.
Event Management: Configure and receive instant alerts for specific events, allowing for quick response to security incidents.
Archived Footage Access: Easily retrieve and review recorded footage, facilitating incident investigation and evidence gathering.
Scalability: Effortlessly add new cameras or sites to the system, ensuring the security infrastructure grows with the enterprise.

With CCTV and IP technologies, advanced surveillance systems enable multi-site operations to be secured effectively. By strategically deploying cameras and integrating centralized management software like ViewStation, security teams have unparalleled oversight and control over their enterprise's safety.
In the following chapters, we will examine access control, intrusion detection, and the role that artificial intelligence plays in enhancing surveillance.
Access Control and Alarm Systems
Access control and alarm systems are critical components of a comprehensive security strategy, especially in multi-site environments.
In this chapter, we explore the various technologies behind access control, the strategic role of alarm systems, and how these elements are specially tailored for self-storage facilities.
Key Access Control Components:
- Electronic Locks and Credentials: Utilize keycards and fobs to control entry. These systems offer flexibility and can be easily reconfigured as access needs change.
- Cloud-Based Access Control: This type of access control offers remote management capabilities, allowing administrators to modify access rights from anywhere, making it ideal for facilities spread across multiple locations.
- Mobile Access Control: Leverages smartphones as access credentials, offering convenience and increased security through encryption and authentication.
The Role of Alarm Systems
Alarm systems have traditionally been a cornerstone of security strategies, providing alerts in case of unauthorized access attempts or other security breaches. However, the effectiveness of alarm systems has been increasingly questioned due to the lack of timely police response.
In light of these challenges, we now recommend professional monitoring solutions over traditional alarm systems. Professional monitoring services, like SCW's Remote Guarding, offer a proactive approach by actively responding to incidents in real-time, which significantly enhances overall security.
Integration benefits of professional monitoring
- Enhanced Situational Awareness: Immediate alerts to security breaches allow for rapid response, minimizing potential damage.
- Active Deterrence: Remote Guarding Officers can alert trespassers that law enforcement is being dispatched.
- Customizable Response: Systems can be configured to recognize different levels of threats and respond accordingly, from local alarms to notifying law enforcement.
Adapting Principles Across Industries
Self-storage is a good example of how security principles can be applied to a wide range of industries, emphasizing the importance of tailored access control and integrated alarm systems. Here's some examples:
Manufacturing: Protect proprietary information and machinery by restricting access to specific areas.
Education: Secure campuses by controlling entry to buildings and implementing lockdown procedures in emergencies.
Healthcare: Safeguard patient records and restricted areas, ensuring compliance with privacy regulations.
Self-storage: facilities present unique security challenges, from providing 24/7 access to customers while safeguarding against unauthorized entry. It is important to balance accessibility with security when planning your access control and alarm systems.
Access control and surveillance systems are indispensable for securing multi-site operations, offering scalable, customizable solutions to meet diverse security requirements.
The next chapter will delve into the future of security technologies, including the role of artificial intelligence and machine learning in enhancing the efficacy of security systems.
Implementing a Unified Security Strategy
Developing and implementing a unified security strategy across multiple locations is crucial for maintaining a secure and efficient operation.
This chapter provides guidelines for creating a cohesive approach to security that encompasses scalability, flexibility, and remote management capabilities.
Developing a Unified Security Strategy
Developing a unified security strategy starts with assessing each site’s unique security needs and risks. This assessment should consider each location’s physical layout, the nature of the business conducted there, and any specific threats or vulnerabilities.
Key Steps to a Unified Security Strategy:
- Risk Assessment: Identify potential security risks at each location to prioritize security measures effectively.
- Technology Integration: Select security technologies that can be integrated across multiple platforms and locations for seamless operation.
- Policy Development: Develop clear, consistent security policies that apply across all locations, ensuring uniform security protocols.
- Training and Communication: Educate employees about the security strategy and their role in its implementation to foster a culture of security awareness.
Importance of Scalability, Flexibility, and Remote Management
For a security strategy to be effective, it must be scalable, flexible, and manageable remotely. Having these attributes ensures that the security system can grow and adapt to changing enterprise needs.
Scalability: Security systems must be able to expand easily to accommodate new locations or increased capacity at existing sites without significant overhauls or downtime.
Flexibility: It is essential to customize security measures for each location's specific needs while maintaining a cohesive overall strategy. This includes adjusting access controls, surveillance coverage, and alarm settings as necessary.
Remote Management Capabilities: Modern security systems offer remote management options that allow administrators to monitor and control security measures from anywhere. This is particularly important for multi-site operations, where on-site management may not be feasible for every location.
Implementing the Strategy
Once a unified security strategy has been developed, careful planning and coordination are required to implement it effectively across all locations.
Technology Deployment: Install the chosen security systems, ensuring they are integrated and function as a unified whole.
Policy Enforcement: Put the developed security policies into practice, with clear procedures for addressing security incidents.
Ongoing Evaluation: The security strategy should be regularly reviewed and assessed for effectiveness, making adjustments as needed based on emerging threats or changes in the enterprise's operational landscape.
A unified security strategy is essential for enterprises with multiple locations. It provides a structured approach to protecting assets, data, and personnel.
By prioritizing scalability, flexibility, and remote management capabilities, businesses can ensure their security measures are robust, adaptable, and manageable from anywhere.
In the following chapter, we discuss the importance of maintaining a secure environment, strategies for maintaining and updating security infrastructure and how to develop a comprehensive response plan for security incidents.
Maintenance, Monitoring, and Response
Maintaining a secure environment is an ongoing process for multi-location enterprises. In this chapter, we examine strategies for maintaining and updating security infrastructure, monitoring options, and the development of a comprehensive response plan for security incidents.
Ongoing Maintenance and Update
A security system's long-term effectiveness depends on effective maintenance. In order to prevent security breaches and system failures, regular system checks and updates are critical.
Key aspects of maintenance include:
- Routine Inspections: Schedule regular inspections of physical and digital security infrastructure to identify wear and tear or technical issues.
- Software Updates: Keep all security software up to date to protect against the latest cyber threats and ensure your systems are running the most efficient, secure software versions.
- Equipment Upgrades: As technology advances, periodically assess and upgrade security equipment to benefit from enhanced features and improved reliability.

Monitoring Services
Monitoring is a vital component of any security strategy, providing real-time oversight of security systems. Enterprises can choose between professional monitoring services and self-monitoring approaches, each with its own benefits.
Professional Monitoring: SCW offers Remote Guarding, a next-generation video surveillance service. Remote Guarding consists of guard watching your camera system to actively react to incidents and alert trespassers that law enforcement is being dispatched. This proactive approach helps prevent crime in real-time and provides an advanced layer of security. Learn more about Remote Guarding here.
Self-Monitoring: For organizations preferring direct control, self-monitoring allows for real-time alerts directly to your phone. This approach requires a dedicated team or individual within the organization to monitor alerts and respond as needed.
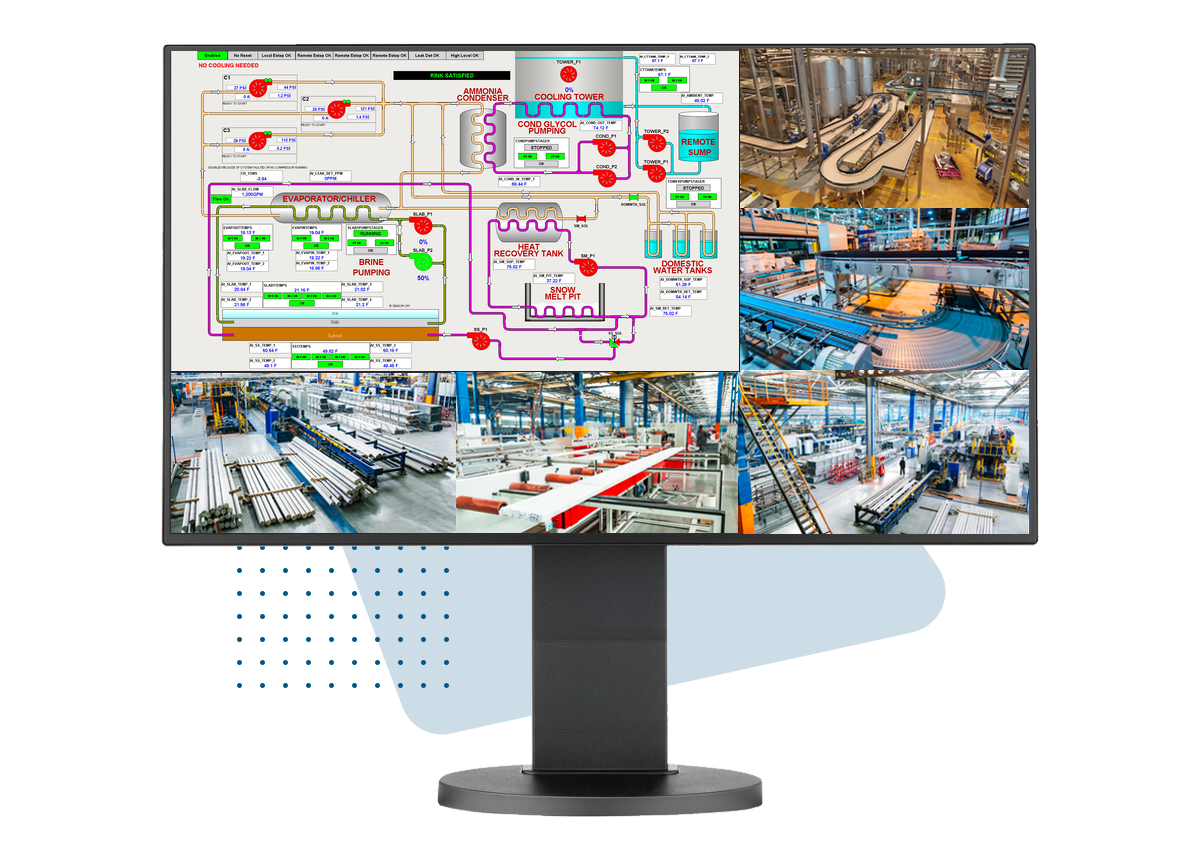
Leveraging Decoders
When self-monitoring process management and other operational departments, it's crucial to incorporate advanced technologies that offer viewing scalability, flexibility, and enhanced capabilities. Decoders are essential for multi-site security operations, especially in settings requiring comprehensive monitoring, such as command centers, guard stations, or process monitoring areas. A decoder is a device that grabs multiple IP camera streams from various cameras or NVRs and displays them on multiple monitors or TVs using HDMI connections. This setup is vital for environments where a broad view of all areas is required simultaneously, ensuring that no detail is missed.
Decoders also play a crucial role in ensuring compliance and operational efficiency. In a manufacturing environment, a decoder can create a live view feed that cannot be altered by the user, eliminating compliance issues by preventing unauthorized changes to the video feed. Retailers, on the other hand, can integrate security with marketing and operational insights by using decoders to display promotional content and operational data.
Developing a Response Plan
A well-defined response plan is essential for efficiently managing security incidents. Quick, coordinated action across all sites can mitigate risks and reduce the impact of security breaches.
Incident Identification: Implement protocols for the rapid identification of potential security incidents through monitoring systems.
Communication Channels: Establish clear, reliable communication channels for reporting incidents and coordinating responses across multiple locations.
Response Coordination: Develop a plan that outlines specific roles and responsibilities for responding to security incidents, ensuring a coordinated effort across all affected sites.
Post-Incident Review: After an incident, conduct a thorough review to identify lessons learned and make necessary adjustments to the security strategy and response plan.
Maintaining, monitoring, and responding to security threats in a multi-location enterprise requires a comprehensive strategy that embraces the latest in surveillance and alarm monitoring technology.
By leveraging SCW's advanced Remote Guarding and Alarm Monitoring services, organizations can ensure their security infrastructure is not only passively recording but actively preventing and reacting to crimes as they happen.
In the final chapter, we explore emerging trends and future directions in multi-location security, keeping your enterprise ahead of the curve.
Future-Proofing Multi-Site Security
In today's rapidly evolving world of multi-site security, anticipating future challenges and embracing technological advances are key to maintaining robust and adaptable security systems.
In this chapter, we provide insights into the future of security technology and offer recommendations for staying ahead of trends to ensure your systems remain effective and flexible.
Anticipating Future Security Challenges
The security landscape is constantly changing, driven by both emerging threats and technological innovations. Anticipating these changes requires a proactive approach:
Cybersecurity Integration: As physical and digital security realms converge, integrating cybersecurity practices into your security strategy will become increasingly important to protect against cyber threats targeting physical security systems.
Artificial Intelligence and Machine Learning: These technologies will play a pivotal role in automating threat detection and response, offering more sophisticated analytics and predictive capabilities to preempt potential security breaches.
Internet of Things (IoT): The proliferation of IoT devices will offer new opportunities for security enhancements but also introduce vulnerabilities that need to be addressed.
Staying Ahead of Security Trends
Continuous Learning and Adaptation: In order to stay informed about new threats and technological solutions, security professionals should engage in continuous learning and adaptation. You can gain valuable insights by attending industry conferences, participating in webinars, and subscribing to security publications.
Vendor Partnerships: Working closely with security technology vendors like SCW can offer access to the latest security solutions and expert guidance on implementing advanced security strategies tailored to your specific needs.
Investment in Scalable Solutions: Opt for security solutions that offer scalability and flexibility to adapt as your enterprise grows and as new technologies emerge. Future-proofing your security infrastructure requires a forward-looking approach that accommodates evolving requirements.
Future-proofing multi-site security is an ongoing process that demands vigilance, innovation, and a willingness to embrace change.
By anticipating future challenges, leveraging advanced technologies and staying informed about emerging trends, enterprises can ensure their security systems remain robust, adaptable, and capable of addressing both current and future security needs.
The Secret to Securing Your Enterprise
As the business landscape continues to evolve rapidly, the security challenges we face are multifaceted. For complete coverage, especially for multi-location enterprises, you need a tailored security solution that protects your physical assets, intellectual property and personnel across various geographical and operational environments.
In this guide, we've navigated through the essential strategies and technologies for securing multi-location enterprises. The focus has been on creating a cohesive and adaptable security framework, from identifying unique security needs to implementing advanced surveillance and access control systems.
The path to securing your enterprise involves a proactive, informed approach, ensuring your security infrastructure not only meets current demands but is also prepared for future challenges. Embrace the journey with confidence, knowing that a well-planned security strategy is a pivotal step towards safeguarding your enterprise's assets, employees, and customers.
To dive deeply into your specific security needs and craft a personalized security strategy, schedule a security review with an SCW expert. Together, we can transform your security challenges into strengths.